PicoCTF Mini 2022 Writeup
Codebook
Question
Solution
They required us to put these two files into a same directory, so I created a new directory called codebook and changed to this directory
Then I downloaded those two files using wget
Then I ran the Python script code.py, which then gave the flag
Flag
picoCTF{c0d3b00k_455157_8100c7c1}
Glitch Cat
Question
Solution
Use nc to see what happen on nc saturn.picoctf.net 52026
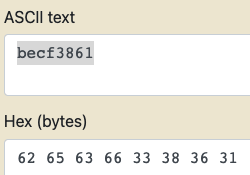
These “chr(0x62)” looks like they are in hexademical, so I use this website to convert those hex to ASCII, which gives the rest of the flag
Flag
picoCTF{gl17ch_m3_n07_becf3861}
HashingJobApp
Question
Solution
Use nc to see what happen on nc saturn.picoctf.net 65352
It requires us to md5 hash the text “babies”, so I use this website called CyberChef(https://gchq.github.io/CyberChef/), which give this result
8374d0764f1466e601c624254222ad53
Lets input this and see what happens
So it seems like there is a timeout mechanic and it will random the text that is required to be hashed, :) so lets do everything above quickly and see if we can get the flag.
Do everything above for a second time, but quickly and see what happens
Interestingly, it requires us to do the md5 hash function for 3 times quickly before getting the flag
Flag
picoCTF{4ppl1c4710n_r3c31v3d_674c1de2}
PW-Crack-1
Question
Solution
Use mkdir to create a directory and change to this directory to later download those two file using wget, to the same directory as required
Using nano to read that password checker file in Python
It seems that if we input “691d” then we can get the flag
Then run this Python script to see if this is true
Flag
picoCTF{545h_r1ng1ng_56891419}
PW-Crack-2
Question
Solution
Use mkdir to create a directory and change to this directory to later download those two file using wget, to the same directory as required
Use nano to read that password checker file in Python
These “chr(0x34), etc” looks like they are in hexademical, so I use this website to convert those hex to ASCII, which gives the password to get the flag.
The password to get the flag is 4ec9, run level2.py to get the flag
Flag
picoCTF{tr45h_51ng1ng_9701e681}
PW-Crack-3
Question
Solution
Simply try all 7 given password to see which is correct
Flag
picoCTF{m45h_fl1ng1ng_6f98a49f}
PW-Crack-4
Question
Solution
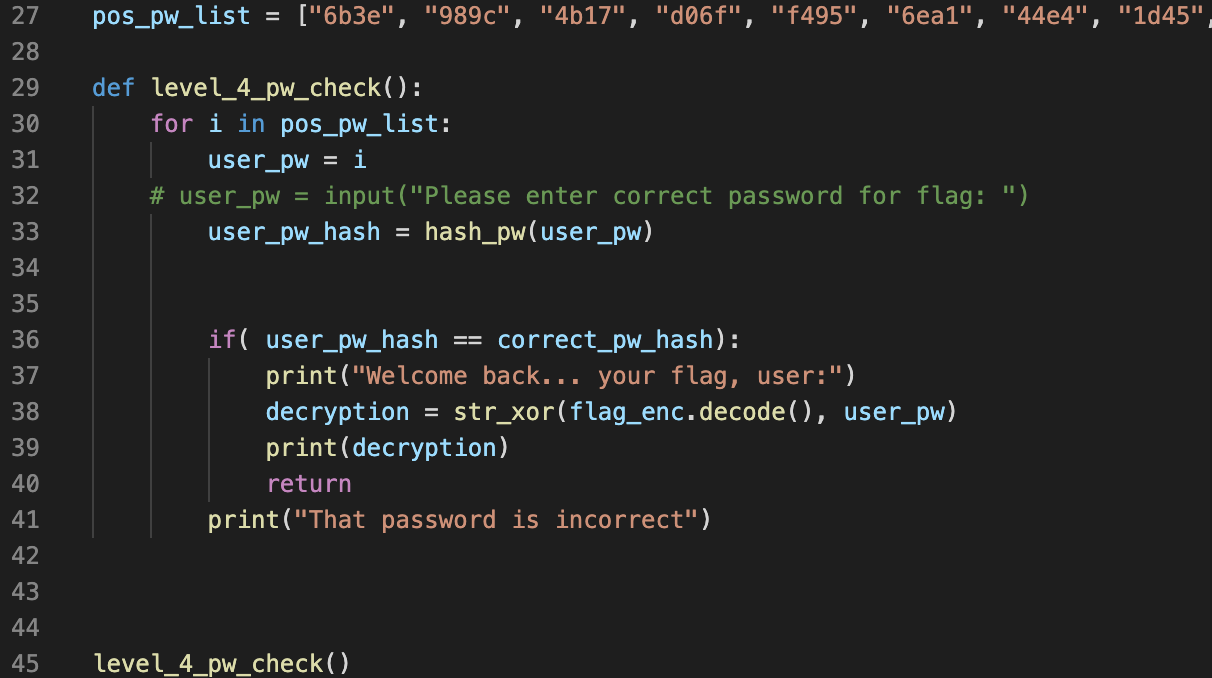
Looking at source code, it looked the same as the PW Crack 3’s source code, the only difference was they gave us 100 strings to check which one is correct instead of 7
So now trying to input each of those strings will not be feasible. thus I edited the source code so that it will automatically try every input for us when the level4.py script run, this used a for loop to do that
Flag
picoCTF{fl45h_5pr1ng1ng_89490f2d}
PW-Crack-5
Question
Solution
Looking at source code, it looked the same as the PW Crack 4’s source code, the only difference was they gave us a txt file, which has a lot of strings, to check which one is correct instead of 100
So now besides using a for loop to automatically try every input for us when the level4.py script run, we also need to edit the code so that it will open and read that txt file appropriately, that is using open() to access these strings and strip() to trim the whitespace from them if any.
Flag
picoCTF{h45h_sl1ng1ng_2f021ce9}
Serpentine
Question
Solution
Use wget to get this Python script
When I tried to run this Python script, it recommended me to check the source code
Take a look at the source code, this part in the code looks like it can give us the flag, basically the flag is the result of the XOR operation between the variable “flag_enc” and the string “enkidu”.
Flag
picoCTF{}
convertme.py
Question
Solution
Use wget to get the given Python script
Then it should stored at the directory you are at, use “ls” to check
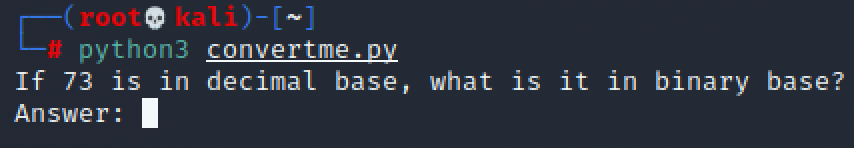
Run the Python file to see what it requires
It requires us to convert a number from decimal base to binary base, so I use this website called CyberChef(https://gchq.github.io/CyberChef/) to help me do this
Now I know the answer of this Python script, lets input this and take the flag :)
Flag
picoCTF{4ll_y0ur_b4535_e2a58836}
NOTE
I strongly recommend everyone new to CTF to use CyberChef as it is easy to use and it has graphical interface. In the beginning I think this will be helpful, along the way you can find some nice software on github that can be used inside Kali Linux or something like that. I found this websire while participating in MetaCTF, which is my first CTF and also my first ever documenting a writeup for a CTF.
fixme1.py
Question
Solution
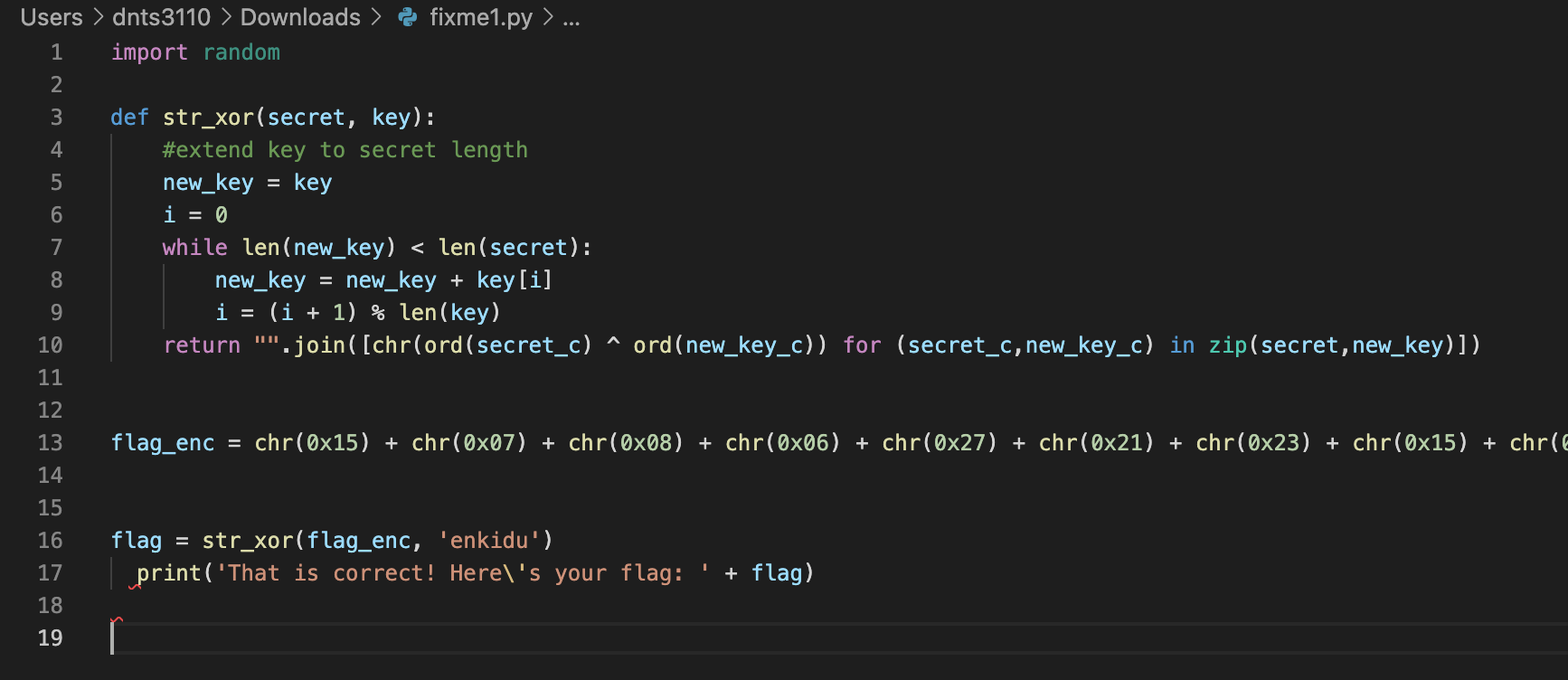
Download the file and use Visual Studio Code that has installed Python Extension to open the file
The syntax error in this Python script is indentation
The fix is going to be remove that indent/space and there should be no syntax error
Then run this Python script to see what happen next
Flag
picoCTF{1nd3nt1ty_cr1515_09ee727a}
fixme2.py
Question
Solution
Download the file and use Visual Studio Code that has installed Python Extension to open the file
The syntax error in this Python script is using operator in python
The fix is using “==” instead of “=” as “==” is an equality operator which would give us true or false based on the condition, while “=” is an assignment operator that is used when we want to assign a value to a variable
Then run this Python script to see what happen next
Flag
picoCTF{3qu4l1ty_n0t_4551gnm3nt_4863e11b}
ncme
Question
Solution
Simply do as what the description said
Flag
picoCTF{s4n1ty_c4t}
runme.py
Question
Solution
Simply do as what the description says
Flag
picoCTF{run_s4n1ty_run}